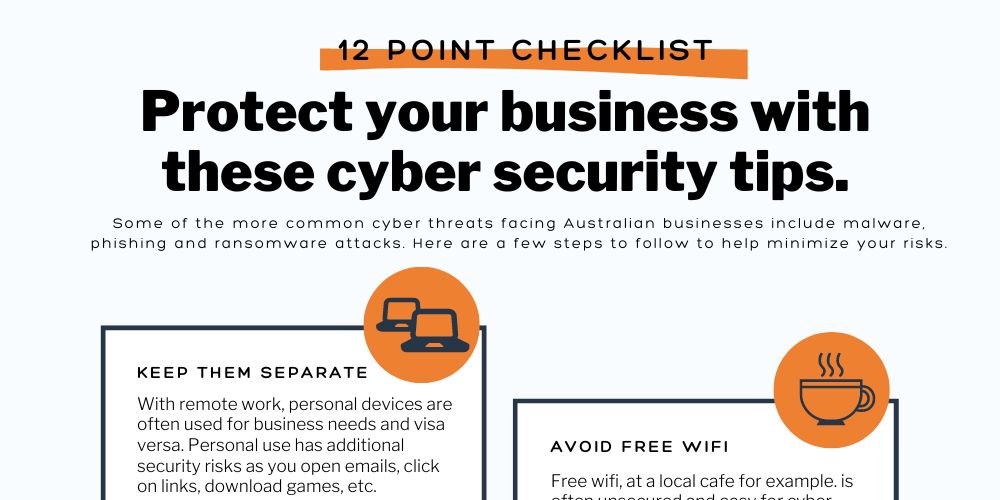
Get Our 12-point Cyber Security Checklist
Our small business cyber security checklist helps you put in place some essential cyber safety measures. This checklist is designed to help small businesses (and their staff) take proactive steps against cyber threats. Avoid:
- Common mistakes employees make when working remotely.
- Simple errors that compromise your network security.
- Frequently used hacking methods.
Download it and feel free to distribute it amongst your staff as a company resource.
“Australian businesses face increasingly sophisticated and capable cybercriminals targeting what matters most to them; their money, data and reputation.”
– The Australian Cyber Security Centre.
There's A Growing Number Of Threats Against Australian Businesses
Australian businesses are facing an unprecedented growth in cyber attacks. The move to remote work, remote connections and virtual file sharing has escalated network vulnerabilities as the opportunity to infiltrate devices and networks becomes more readily available.
Most Common Cyber Attacks
‣ It takes on average of 4mins for a hacker to infiltrate a network via email attacks, 286 days to be detected and 80 days to resolve the damage.
‣ The estimated cost of cyber crime to Australian businesses per year is $29Billion.
What Are You Waiting For?
According to the ACSC, most Australian small businesses know that cyber security is important, but don’t do anything about it. They face ‘barriers’ to implementing good cybersecurity practices, such as:
- Not having enough IT staff with sufficient security focus or training.
- Most small business owners fail to recognise the weaknesses in their own IT infrastructure
- Not knowing where to start to fix the vulnerabilities.
- Small business owners lack time to sufficiently plan and respond to this critical issue.
One of the best ways to plan, protect and respond to these threats is to outsource your security posture to an experienced IT service provider like 9sphere’s Technologies. We’ll start by running an audit of your existing security and identify any vulnerabilities and existing threats. From there we can implement a world-class, proactive cybersecurity management system.
Chat to us for more information, and in the meantime, download our free cyber security checklist and get the essentials in place.

